Critical PAM controls for modern cloud environments
- Critical PAM controls for modern cloud environments







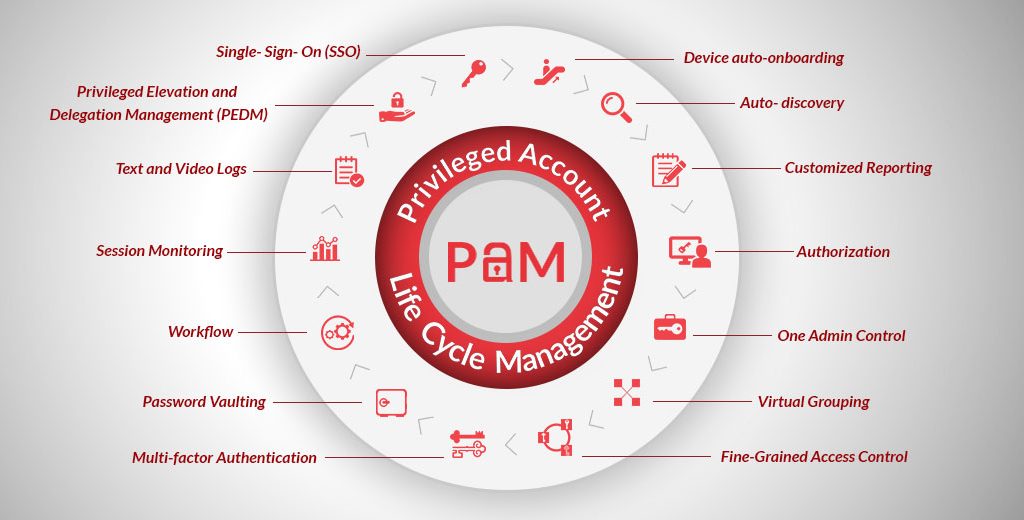
Failures and breaches in cloud security are often brought on by improper administration of user identities, permissions, and other related factors. A research by Gartner titled “2019 Innovation Insights for Cloud Security Posture Management” made the following claims:
In other words, the problem isn’t with cloud security per se, but rather with the laws and technologies that govern and regulate it. The user, not the cloud service provider, is usually to blame for poor control management.
According to McAfee, businesses face an average of 4.3 cloud risks every month from sources such as external hackers, malevolent insiders, and accidental blunders. Because of this, 80% of businesses have had at least one account hacked.
Because of how heavily we rely on cloud services, we need to modify our IT policies and procedures to accommodate this new way of doing business. In this article, we will examine the various cloud applications and the essential Privileged Account Management (PAM) rules that can protect your business from cyberattacks.
Infrastructure-as-a-Service (IaaS)
According to McAfee, incorrectly configured IaaS is a leading cause of cloud security failures and breaches. Misconfiguration issues may easily reach the thousands per month if even a small number of IaaS instances are operating with incorrect settings.
Setting “open write” permissions is said to be another typical IaaS misconfiguration mistake, which might allow hackers to steal and destroy your assets and private data.
Through PAM for the cloud, businesses can safeguard themselves against IaaS vulnerabilities and decrease risk. Using PAM, you may restrict access to the cloud control panel for all key resources and oversee continuous access to cloud-based services, therefore protecting the root accounts of servers set up in the cloud.
Setting up Continuous Integration and Continuous Deployment in a DevOps Setting
It’s very uncommon for DevOps approaches to inadvertently open up security holes in privilege management, making the system more susceptible to assault by malicious actors. DevOps teams rely heavily on cloud services because they allow them to rapidly install and expand containers, servers, and apps across a wide variety of settings.
DevOps teams rely heavily on on-demand access to cloud-based apps and databases for system administration and bug fixing.
You can secure the communication between DevOps systems, as well as the communication between those systems and databases, applications, and enabling systems, and do away with the need for hardcoded credentials by making API calls to a secure PAM vault, all with PAM designed specifically for cloud use cases.
software as a service
Human-generated passwords are a major security risk for businesses because they are easily cracked, are often shared among employees, and are frequently used for more than one account.
Though “123456,” “qwerty,” and “password” are among the most frequently used user-generated passwords, they are also among the easiest for hackers to guess.
If a user’s credentials are stolen and the hacker knows the user’s email password, LinkedIn password for work, and Dropbox password, the hacker might have access to all of the user’s stored information.
AML integration enables uniform settings for password complexity and rotation, and PAM controls may assist reduce the risk of SaaS services by offering browser plug-ins for single-sign-on to inject saved credentials into browser-based SaaS tools.
When it comes to solutions for managing permissions in the cloud, Thycotic is unrivalled. Over 10,000 enterprises, from startups to the Fortune 500, rely on Thycotic’s security solutions to reduce the risk of privileged accounts, implement least privilege rules, manage applications, and prove compliance.
What Should Be Done Next?
The CV-19 pandemic has been used in an alarming increase of phishing and ransomware assaults throughout the IT sector. In order to prevent businesses from paying ransoms and restoring their IT systems, cybercriminals have been specifically targeting backup systems.